Malware: Trojan Horse
The Trojan Horse – A Deceptive Trap
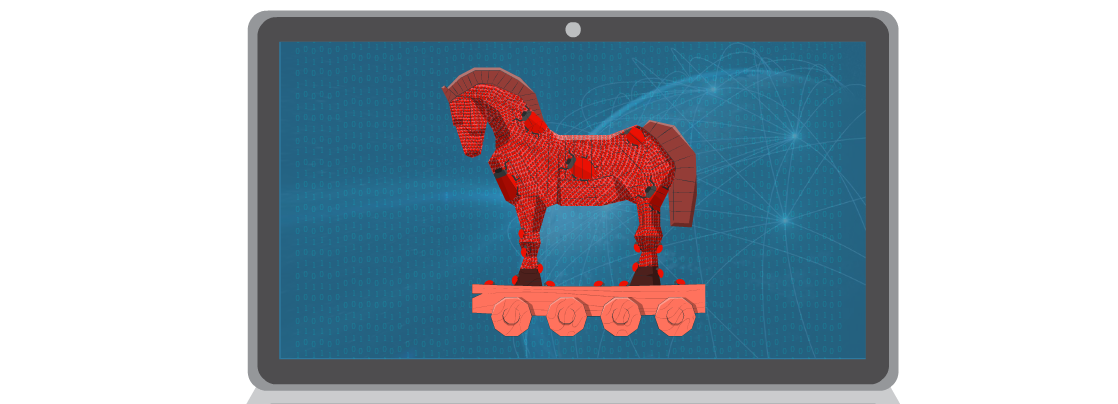
The legend of the Trojan Horse tells of how the Greeks tricked the Trojans into bringing a hidden army inside their city walls, leading to their downfall. Similarly, Trojan malware disguises itself as a harmless file or software, tricking users into installing it. Once inside, it can steal data, corrupt files, or create backdoors for hackers.
How Trojans Work
Like the legendary wooden horse, a Trojan horse is malware disguised as legitimate software, tricking users into installing it. Once activated, it can steal data, compromise security, or grant hackers unauthorised access. Unlike viruses, Trojans don’t replicate themselves but rely on deception. They often appear as free software, email attachments, or fake updates. Once installed, they can;
- Steal passwords and financial data
- Monitor user activity (keylogging, spying, etc.)
- Delete or corrupt files
- Open backdoors for cybercriminals
Notorious Trojan Attacks
- Beast (2002) – Gave hackers remote control of affected computers.
- Zeus (2007) – Stole banking details.
- Emotet (2018) – Spread malware across networks.
- ZeroAccess (2021) – Used infected systems for illegal activities.
How to Stay Safe
- Avoid suspicious downloads – Only install software from trusted sources.
- Be wary of email attachments – Don’t open files from unknown senders.
- Use strong antivirus protection – Regular scans help detect threats.
- Keep software updated – Security patches fix vulnerabilities.
Conclusion
Just like the Trojan Horse of ancient Greece, modern Trojans deceive their victims, often with disastrous consequences. Staying alert and following cybersecurity practices can help protect your system from these hidden threats.